
User Entity and
Behavior Analytics
Leverage Machine learning-based threat detection and user behavior analytics to protect and bolster your enterprise security posture.
What is UEBA?
- where do users log in from?
- what devices do they log in from?
- what file servers and applications do they access?
- what privileges do they have?
How UEBA Works
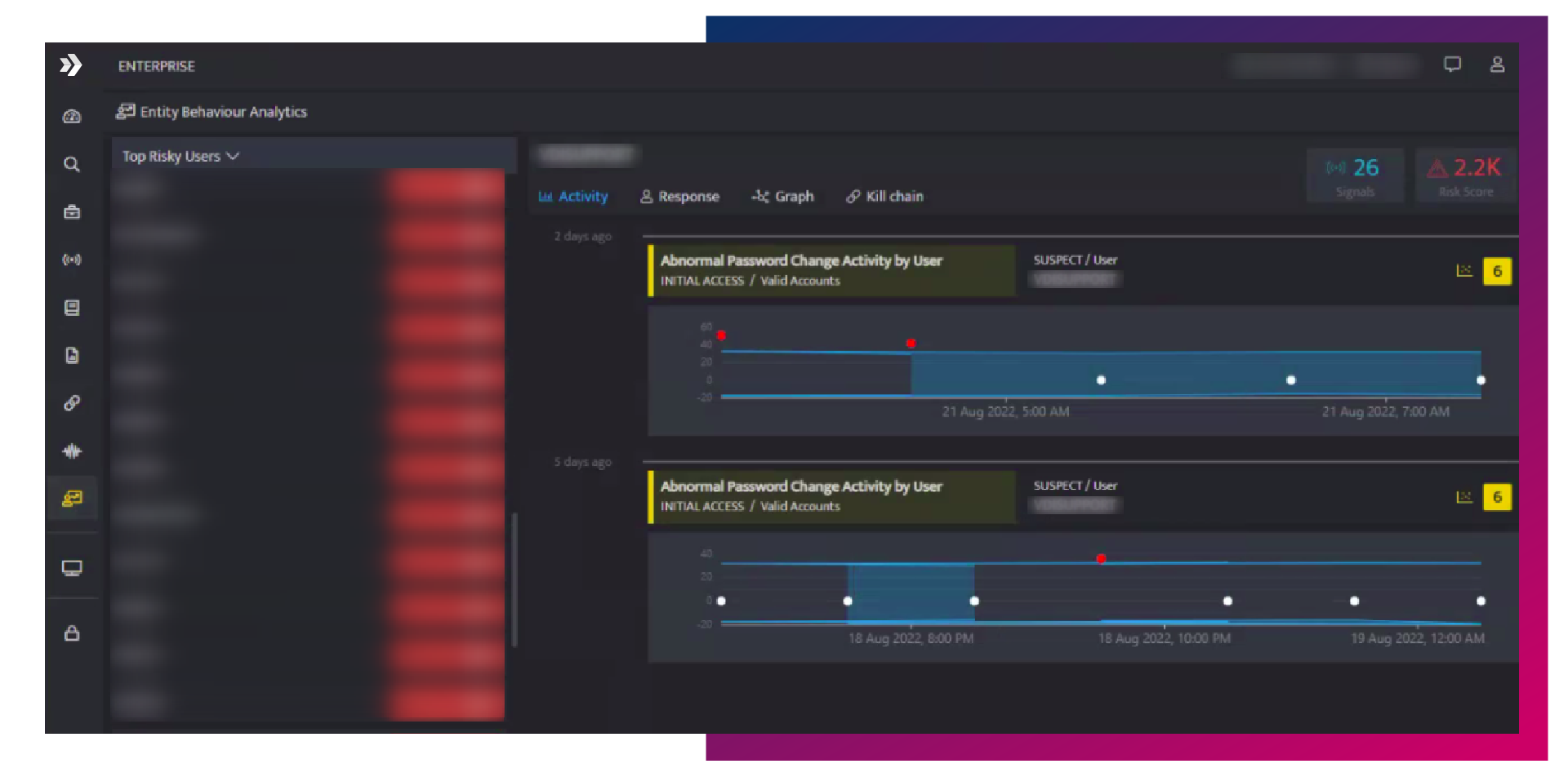
Why you need UEBA?

Policy or rule based approaches are not able to detect subtle, risky behaviors. Behavior analysis based on raw activity data, helps in identifying users based on rogue intent.

Historical analysis provides deeper insights into usage and trends based on statistical analysis and pin points threats that may occur over a much more extended period of time.

Dynamic baseline for user and device behavior based upon normal behavior. A behavioral profile for each applicable attribute of a user or entity is created using data science.
Ready to See UEBA in Action?
Book a personalized demo to see how your security operations can leverage UEBA.
Why DNIF
DETECT THREATS, NEVER SEEN BEFORE
Determine users exhibiting risky behavior such as privileged access and atypical data movement.
LOWER RISK & REDUCED ATTACK SURFACE
Analyze and detect patterns of human behavior in big data to reduce the attack surface.
IMPROVED OPERATIONAL EFFICIENCY
DNIF learns from the anomalies you find most valuable, and then screens out irrelevant detections.
CUSTOMIZABLE RISK MODELS
Data models informed by both structured data, such as SIEM logs and unstructured data.
TREND ANALYSIS
Historical analysis allows you to quickly learn and profile user / entity / parameter behavior.
DETECT OUTLIERS
Leverage ML models to detect and make high-level decisions around your security posture.
Customers that Love and Trust us





Ready to make your security operations even better?
See what makes us different. Book your personalized demo today and see DNIF in action.

