CLOUD NATIVE Platform
built for
DNIF HYPERCLOUD helps you minimize your time to value and take data-driven decisions swiftly.
Designed to Improve Operational Efficiency
-1.png)
More Automation. Less Tuning. Faster Detection
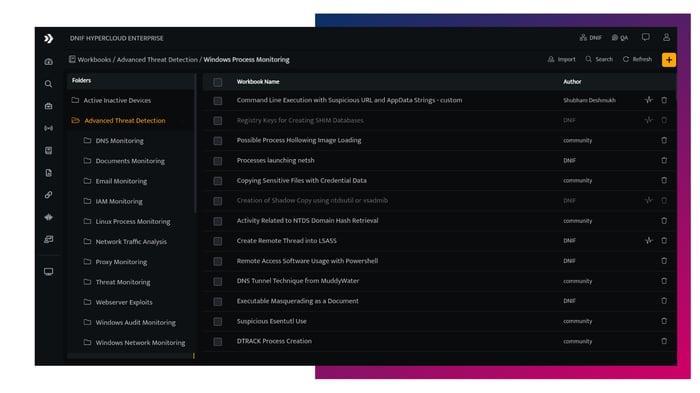
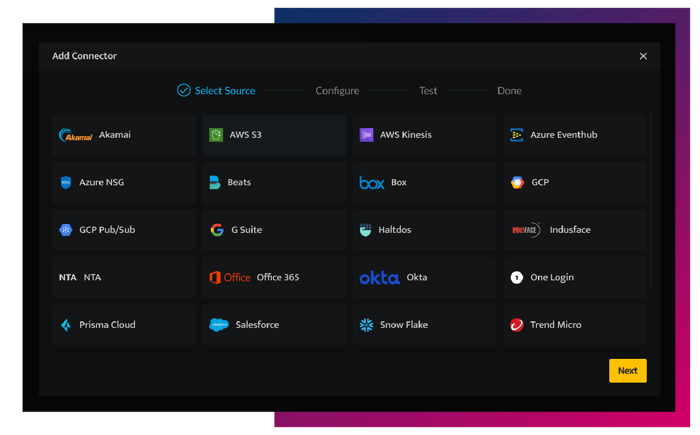
Event Source Onboarding
- Log Source Integration
- Security Data Lake
- Support for 100+ Enterprise Event Sources
Native Connectors for easy onboarding of log data in any format or protocol. Both for on premise and cloud workloads.
- Autodetection Engine
Automatic identification of log format and source type. No configuration needed. - Just point your logs to the HYPERCLOUD and forget. It’s that easy.
- Distributed Filer
Framework built for modern high-speed storage, lossless compression and parallel data processing at petabyte scale. - 365 days of retention
We enable you to store what’s needed as long as it’s needed without breaking the bank. - Online Hot Storage
We don’t believe in archives and having storage tiers. All the data you ingest with the HYPERCLOUD is kept hot and always queryable.
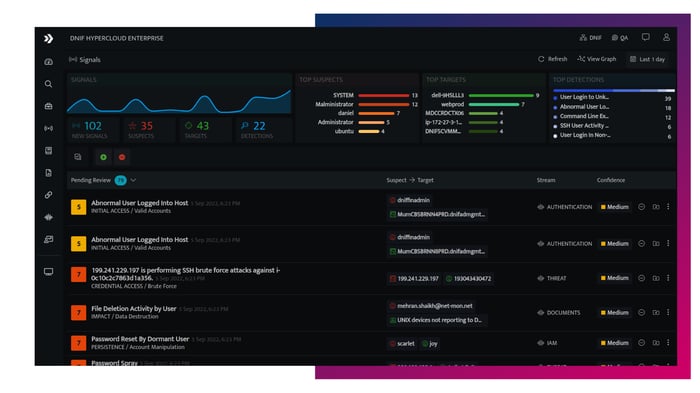
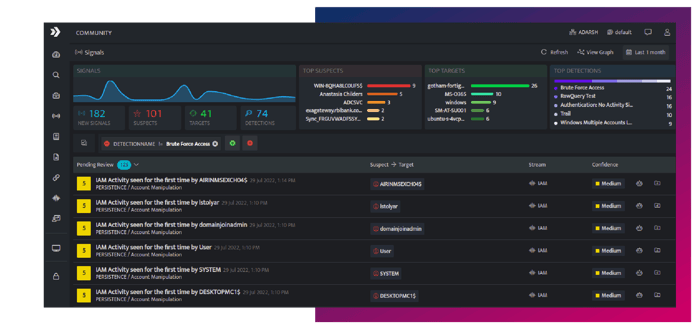
Threat Detection
- Active Content
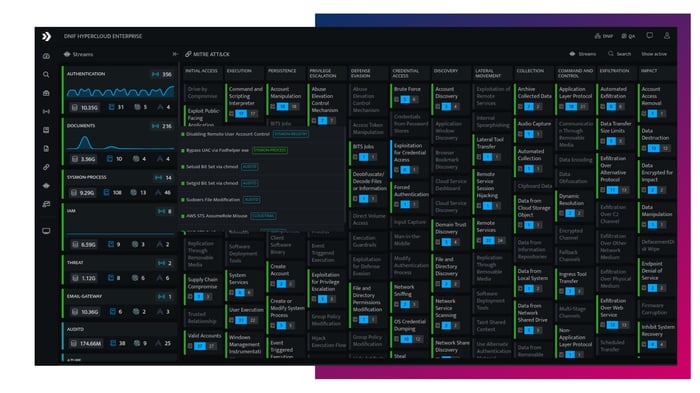
- MITRE ATT&CK Framework
- 500+ Threat Detections
Out-of-the-box workbooks annotated with confidence levels, killchain and TTP mapping aligned with the MITRE ATT&CK framework. - Continuous Threat Monitoring
Maps detection content continuously with incoming data to identify signals in the noise and track potential events of interest. - Active Threat Content
Instant access to new threat detection content, dashboards, extractors and indicators of compromise. Spend less time on security detection engineering and more time investigating and responding to threats.
- Tightly integrated with MITRE ATT&CK across all primary product capabilities from signals to graphs to machine learning.
- Detection content is annotated by our Security Research team with confidence levels, killchain and TTP mappings.
- Prioritize event sources that boost visibility and detection to ensure maximum coverage of adversarial tactics, techniques and procedures.
Investigation
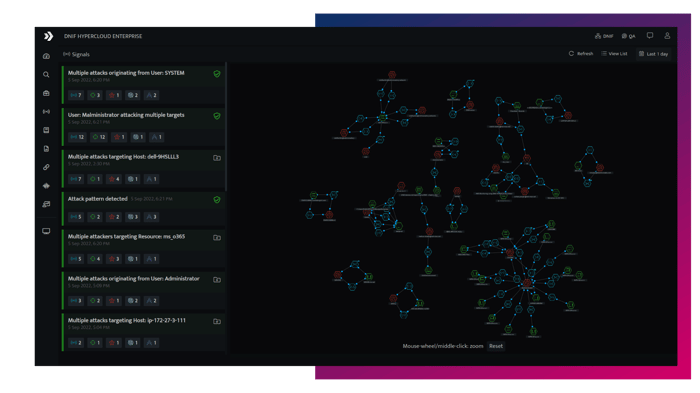
- Graph Analytics
- Context Convergence
- Connected Signals
Our graph engine continuously finds and builds connections between entities seen in monitored telemetry helping you connect the dots and uncover complex threats faster. - Uncover APTs
Connecting signals provides more situational context, uncovers larger adversarial campaigns and allows analysts to make decisions faster. - Accelerate Triage
Reviewing graphs versus individual signals helps you accelerate triage and ensure no alert slips through the net.
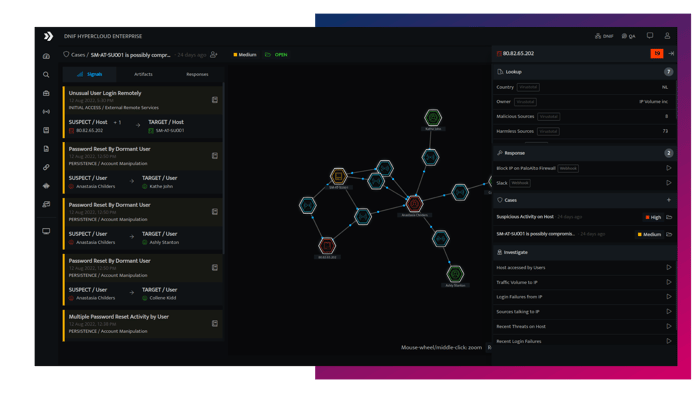
- One-Click Context
With just a single click, analysts can access complete context for what triggered the signal, from raw events right down to the processes, command lines and hashes. - Internal and External Intelligence
Access identity, asset and business information through integration with IAM, custom enrichment datasets and IT inventory management systems. Access Threat Intelligence through integration with VirusTotal, URLHaus and other 3rd party data sources. - Convergence
Converged context enabled by the investigate panel allows analysts to quickly determine the priority of signals for incident response. Customizable workflow to automate validations and repetitive actions with automation plugins.
Security Analytics
- Workbooks
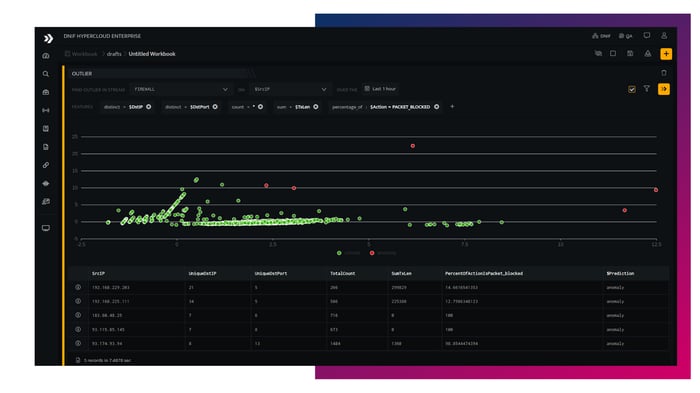
- Outlier Detection
- No-Code Machine Learning
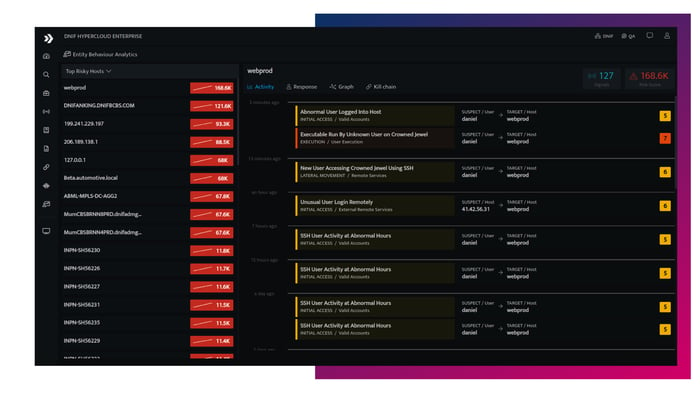
- The UEBA Advantage
- Multi-stage Detections
Stitch together multi-stage logic for detection, decision-making and response automation with a combination of search, data transformation, correlation and external integration. - Notebook-Style Analytics
Workbooks support multiple building blocks for leveraging DQL, SQL, Sandboxed Python, Outlier Detection, Markdown, Reference Datasets, Visualization, Alerting, Signal Generation, Lookups and Responses over APIs and SSH. - Autonomous Security Operations
Workbooks power our entire analytics stack from detection to dashboards to reporting and are the building blocks for autonomous security operations.
- Identify outlier entities based on prevalence and statistical features using on-demand Multivariate Outlier Detection.
- Coupled with the identity and asset enrichment capabilities of the platform, this becomes a great starting point for threat hunting or ad-hoc investigations.
- Works on both incoming data streams as well as historical data.
- Time-Series Anomaly Detection
Baseline access patterns, geolocations, activities and more to spot anomalies with a fully managed no-code framework. - Activity Profilers
First Seen and Rarity Profilers help you track high-privilege activities on critical infrastructure or crown-jewel assets. - 100+ use-cases
Access a catalog of hundreds of out of the box ML models created by our Security Research teams.
Like what you see?
Request a personalized demo to see how DNIF HYPERCLOUD is better than your existing SIEM.


.png?width=700&name=ScreenShots_V2-03%20(1).png)